- Interview the IT departments of some of the companies that were affected by 9/11. See this list.
- Go read
-
 Fire in the computer room, what now?.
Fire in the computer room, what now?. - Try Automating
UNIX and Linux administration
- Microsoft has an interesting page about reliable computing. I should probably add something about Microsoft systems.
- Read articles on the Wikipedia
- Read pages on the internet
- Interview Edmond
-
We've used Hunt Engineering (www.hunteng.com) for datacenter mechanical
and electrical engineering. I haven't personally worked with them, but
the results and feedback from coworkers were very good.
Troy
_______________________________________________
Members mailing list
Members@lists.seattle-sage.org
http://lists.seattle-sage.org/mailman/listinfo/members - Reread

DeMarco, Tom. Controlling Software Projects: Management, Measurement and Estimation.
Englewood Cliffs, NJ: Prentice-Hall, 1982.
Dorset House, New York, 1995. ISBN 0-932633-34-X.
--State of Information Security 2005 Report Finds Security-Related
Events on the Rise
(12 December 2005)
The State of Information Security 2005 report from CIO Magazine and
PricewaterhouseCoopers found that security-related events have increased
22.4 percent since last year. Just 37 percent of the companies
responding to the survey have established a security plan; twenty-four
percent plan to implement one in the next year. The number of
organizations with a CISO or CIO rose from 31 percent last year to 40
percent this year. Among organizations with a chief information
security officer (CISO) or Chief Security Officer (CSO), 62 percent have
security plans in place. The study surveyed more than 8,200 IT security
executives in 63 countries around the world.
http://www.enn.ie/frontpage/news-9658009.html
http://www.siliconrepublic.com/news/news.nv?storyid=single5805
[Editor's Note (Schultz): The fact that only 37 percent of the companies
that responded to this survey have a security plan is not a very good
sign. I fear that Donn Parker may have been right when he asserted that
the practice of information security is more like "folk art" than
anything else. ]
- S&M
- Goals of measurement
- What works and what doesn't
- capacity planning
- identify systems for sunsetting
- Things to measure
- uptime
- software defect density
- hardware reliability
- machines ready to sunset
- Access logs
- Error logs
- Value of processes
- Uses and abuses of the data
- A quote from SANS:
ARRESTS, CONVICTIONS AND SENTENCES
--Engineer Indicted for Alleged Theft of Trade Secrets
(23 December 2005)
An engineer has been indicted for alleged theft of trade secrets.
Suibin Zhang allegedly downloaded proprietary files from Marvell
Semiconductors, Inc, after accepting a position with Broadcom, a Marvell
competitor. Zhang had access to the Marvell data because his former
employer, Netgear Inc., was a Marvell customer. Zhang then allegedly
loaded the files onto a Broadcom-issued laptop and emailed some trade
secrets to other Broadcom employees. Zhang entered a not guilty plea
and was released on a US$500,000 bond. If convicted on all counts,
Zhang faces a maximum jail sentence of 75 years and a fine of in excess
of US$2 million.
http://www.eetimes.com/showArticle.jhtml?articleID=175400269
[Editor's Note (Honan) Most companies access policy disables user
accounts for employees who have left the company. This is an example
of how that policy should be extended to include external users from
partner companies or suppliers with employees who have access to
sensitive data.]
- Site location - don't go in a high rise! Don't go in a
basement! Ground floor or second floor is best.
- Physical Security. Floor to true ceiling walls, be wary
of hanging ceilings. Access controls. Personnel security
for both you and your vendors.

- Small onsite staff for repairs and installations (and deinstallations), larger ops staff elsewhere
- Disaster recovery site
- Design for reliability
- Predicting reliability
- Reducing failure through redundant systems
- Reducing failure through highly reliable systems - internal
redundancy
- Reducing failure through increasing quality
- Improving MTTR
- The goal: "lights out" computing

- logging - syslogdng, log file processing, mod_log_spread.
What doesn't work.
- disaster recovery site
- distributed database
- redundant SSH daemons on different ports (see port scrambling)
- Scripting and script cookbook
- who's hitting the webserver?
[root@angel root]# for i in `fgrep -h finao /var/log/httpd/access_log* | awk '{print $1}' | sort | uniq`; do
> host $i
> done
Host 25.2.168.192.in-addr.arpa not found: 3(NXDOMAIN)
244.29.188.207.in-addr.arpa domain name pointer tog-wakko4.prognet.com.
119.98.46.207.in-addr.arpa domain name pointer msnbot.msn.com.
Host 236.149.119.62.in-addr.arpa not found: 3(NXDOMAIN)
16.64.249.66.in-addr.arpa domain name pointer crawl-66-249-64-16.googlebot.com.
42.64.249.66.in-addr.arpa domain name pointer crawl-66-249-64-42.googlebot.com.
165.66.249.66.in-addr.arpa domain name pointer crawl-66-249-66-165.googlebot.com.
40.71.249.66.in-addr.arpa domain name pointer crawl-66-249-71-40.googlebot.com.
41.71.249.66.in-addr.arpa domain name pointer crawl-66-249-71-41.googlebot.com.
[root@angel root]# - Populating the equipment database
- Configuration management
- Problem ticket system
- Change control using RCS, CVS or perversion
- Set up repositories for system software and for each project
- check in code
- move code between environments
- check out code to dev, int, load, test, production environments using tags
- reverting
- fallback planning
- security
- The philosophy of security
- Separating identity, authenticity, and authorization
- The roles of kerberos, LDAP and NIS
- Active Directory
- port scrambling
- Reliable software (This
is misplaced)
- Windows just doesn't cut it (From 16-Dec-2005 SANS mailing
list):
--Versions of Windows Server 2003, Windows XP Receive Common Criteria
Certification at EAL 4+
(14 December 2005)
Six versions of Microsoft Windows Server 2003 and two versions of
Microsoft Windows XP have earned Evaluation Assurance Level (EAL) 4+ of
the Common Criteria. Meeting the standards set by the Common Criteria
is necessary to win federal contracts that involve dealing with
classified information.
http://www.fcw.com/article91728-12-14-05-Web
http://appserv.gcn.com/cgi-bin/udt/im.display.printable?client.id=gcndaily2&story.id=37775
[Editors' Note (Schultz): Achieving EAL 4+ certification is no small
feat. Microsoft has truly made a lot of progress when it comes to
security in its operating systems.
(Guest Editor (Donald Smith): Microsoft windows evaluation was against
the CAPP. From: http://niap.nist.gov/cc-scheme/pp/PP_CAPP_V1.d.pdf
"The CAPP provides for a level of protection which is appropriate for
an assumed non-hostile and well managed user community requiring
protection against threats of inadvertent or casual attempts to breach
the system security. The profile is not intended to be applicable to
circumstances in which protection is required against determined
attempts by hostile and well funded attackers to breach system
security."
(Multiple): When a government agency says a product meets a high
security standard, and that is a product in which dangerous flaws are
continuously discovered and for which the vendor chooses not to release
an existing patch while exploits for the flaw are circulating on the
Internet, perhaps the standard (Common Criteria) is part of the problem,
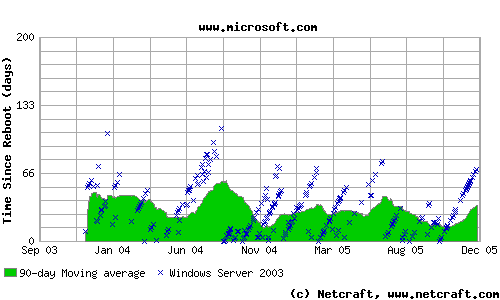
and should be reconsidered.]Microsoft
Commerical Ventilation and Vacuum (home of Failure is Not an Option)
Real Networks
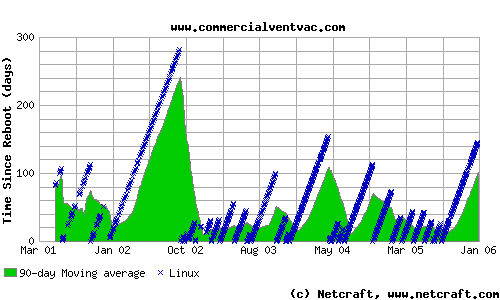
Running linux and apache
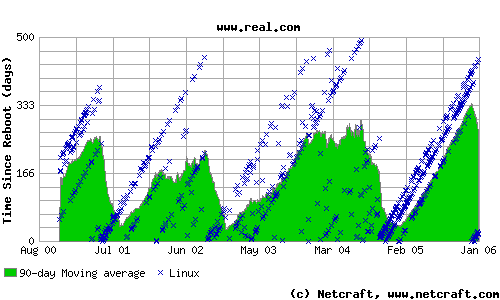
Running Linux and coyote
California Institute of Technology
Hewlett-Packard
National Cash Register (NCR)

Running Linux and AOLserver/3.3.1+ad13 Running HP-UX and Apache
(impressive)
Running HP-UX and Apache
(impressive)

NCR (underwhelming)
Match.com
MacWorld Expo
My server world

Windows Server/2003 and IIS

Windows server 2003 and IIS

Windows server 2003 and IIS
- Kernel panics, blue screens of death, kernel logging
- Access control
- Bastion host
- Authentication server
- NIS
- Kerberos
- LDAP
- Active Directory?
- Public keys
- selinux
- file system security and how to test it
- Application security
- non-stop Software updates
- testing
- Monitoring
- SNMP
- Customer view monitoring
- Internal only monitoring
- PC vs Web-based vs VT100 based (or thick client, thin client, anorexic client)
- The "known problem" problem
- Backups
- What if somebody steals a backup?
- Backups on tape vs. sent electronically
- readonly, read mostly and read/write data. Metadata
- Recovery
- Special considerations for the registry in MS-Windows/NT,
2000, 2003/server, longhorn/vista
- Load balancers
- Dedicated load balancers
- keepalived
- Linux Virtual Server
- Application based load balancers
- Hot standbys
- Warm standbys
- Cold standbys
- file systems
- unmount /boot, mount /bin, /sbin, /usr readonly, mount /etc /home /var /tmp read-write
- chroot jail
- ext3 vs. ext2 vs. GFS
- The problems with NFS
- locking files against simultaneous access.
- Moving data: rsync, scp
- Hardware
- White box vs. a brand name (whatever happened to DEC?)
- Dual power supplies - get short power cables
- RAID
- Remote management hardware - BMC cards (IPMI) DRAC
- smartd
- Networking
- Security
- VPNs and LANS
- asssymetric routing
- Utilities
- DNS
- NTP
- DHCP
- arpwatch
- Fiber optic vs UTP
- Testing
- Test plans and objectives
- Regression testing
- Failure testing
- Test environments
- dev
- int
- test
- load
- production
- ancillary
- Virtual machines, IP address aliases
- post release testing
- Operations
- Policies, procedures, and documentation
- Drills
- training
- Common failure modes
- Power problems
- cooling problems
- IP addressing problems
- Equipment database
- location
- Update from DNS, arp
- Inventory control
- pointer to documentation
- How to deal with exceptions (one-of), multiple IP addresses, change of equipment, virtual machines
- Machine room organization
- Air flow
- Racks
- Cable Management
-

- A case study
- Design
- Implementation
- testing
- Acknowlegements page and resources page.
- Page last modified java script
- Navigation links (how to do that? Use a program?)
- HTML to Docbook translator?
- Cartoons:
- Who knows what clowns facilities is letting into the data closets? (A clown entering a room labeled "data closet"... and he's carrying a hacksaw)
- Measuring user satisfaction is always a good idea (a sysadmin has his feet on his desk and is talking on the phone about something he read on slashdot. Meanwhile, his users are approaching with torches, pitch forks, shovels and boy do they look mad!)
- Test your backups before your customer's computer fails (One man is chasing another with an ax while in the background is a computer with wisps of smoke coming from it)
- Cable management is useful (A rack with cables going every which way. In the middle is a bubble coming from the mass with the word "help?"
- Reliability testing (a devil pulling a wire from the back of a computer)
- Lights out computing. (Before and after: A person grinning broadly reaching out for a lightswitch and standing next to a rack full of wires. Hidden in the rack is a cat. After, the room is pitch dark except for the eyes of the sysadmin, the teeth of the sysadmin, and the eyes of the cat).
- The medievel model of computing: in a clearing is a castle, surrounded by a moat, with high walls, battlements, a high tower, with a stout door, and a princess in the tower.
- "Good morning, your network is about to go down" As
the sun is rising, a huge earth scooping machine is about to take a
slice out of the ground.




